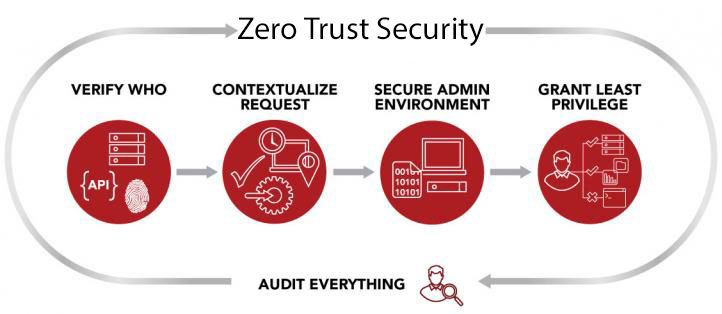
The idea of zero trust security has been around for several years. It has grown in popularity rapidly through 2020 and 2021 as Covid 19 has forced many businesses to work from home and looks to become the new standard for securing a mobile workforce. It will be key to most security strategies moving forward […]
Most IT guys are innocuous. On occasion, you find and IT guy that is well meaning but dangerous. How is he dangerous you ask? I’m not talking about him going rogue and sharing confidential data, or maliciously shutting down your network. The danger he poses is more accidental than purposeful, however it can still destroy […]
Phishing attacks are becoming more and more sophisticated as technologies advance. Cyber criminals are finding new ways to trick people into giving up their credentials, banking information, or other sensitive data. Attackers use many different techniques to break into systems including building fake websites that look authentic, sending emails disguised as being from companies you […]
I met with a company this week that is thriving. They have been growing by leaps and bounds over the last couple of years, and its run by smart, talented people. The one area where they are struggling is with managing their technology. That’s why they called me. They were essentially asking how to tell […]
The High Cost of Holding on to Antiquated Technology I got a call recently from a business owner that desperately needs our help. Their network is in shambles. They have multiple overdue projects, and the old technology they have in place is costing them time and gumming up their business processes. It’s not the worst […]
Not every managed services provider (MSP) is the same. Your business has unique needs, all of which need to be handled by your MSP. Your MSP should understand how to improve regulatory compliance, protect your IT infrastructure, and improve business efficiencies. Some IT providers are better equipped than others to handle these needs. Your managed […]
Cybersecurity resilience is the ability of an organization to maintain its operations in the face of cyberattacks. It’s important because it helps protect your data and systems from damage or theft and allows you to recover quickly if an attack occurs. There are many things you can do to improve your cybersecurity resilience, including: Govern […]
Antivirus solutions have been continually evolving over the years along with threats and attack patterns. Endpoint detection and response (EDR) is the latest evolution and offers some significant advantages over its predecessors. It’s been a long journey. Here is a brief timeline of AV evolution and some practical advice about the very real advantages of […]
Clark sat at his desk staring at his monitor, the frustration mounting. He felt tired. He loved his work, and he was damn good at it. This was simply too much. He had started work at a new company a few months prior. As an IT administrator he was excited to get his hands dirty […]
The news is full of the latest companies that have suffered security breaches. These headlines focus on large corporations because the big numbers involved make the attack more impressive. This gives many small business owners a false sense of security -an illusion that there is security through obscurity. There is an idea that a “small […]