While many shortcuts are similar on both PC and Mac computers, a Mac has a few different keys that make its shortcuts slightly different. If you are new to a Mac, transitioning from a PC, or simply want to know how to do your work faster on your Mac, here are a few of the […]
Category Archives: Blog
For those of you who love your PC and are constantly on the lookout for ways to improve your performance, this is a list for you. Keyboard shortcuts can help improve the speed with which you perform basic functions, helping you eliminate the clunky necessity of moving back and forth between your keyboard and your […]
Too often, computer and network security is not thought about until a problem arises. At this point, a breach in security can cause huge and potentially harmful problems to your business and/or your customers. By setting up a security plan and an emergency action plan, you can know that the information held in your computers […]
Having reliable data is a critical component of running a successful business. It can help you to make really good decisions and prevent you from making really bad ones. One area of business information that is often sorely neglected and overlooked is technology data and reporting. Having some good data on the status of your […]
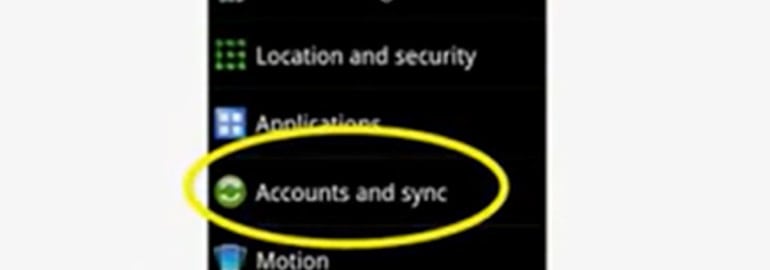
In this tutorial we will give a basic overview on how to setup your Android device to Office 365 Service as a first time setup. The screen shots have been taken of an Android phone. Please note that all Androids are slightly different so it’s possible that your device may require slightly different steps than […]
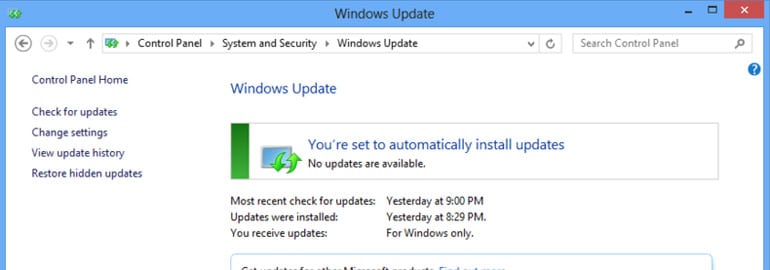
We’ve all had Microsoft Windows pop up and let us know that it needs to be updated at one point or another. What are those updates? Are they important? What happens if I don’t do them? They are important, and they do need to be done. Here’s why. Microsoft updates are basically broken into 4 […]
There so many hardware choices out there that business owners are often left scratching their heads as to what hardware choices to make to get the best ROI. The answer depends very much on the nature of your business and what you do with the hardware, but below are some general guidelines that can help […]
The new rage in mobile computing is the tablet, but some businesses have been left scratching their heads on how they can successfully integrate these devices into their networks. The main issue with most tablet devices is that they don’t run an operating system that is compatible with the business applications that you use on […]
Below are the steps on how to add an Exchange account to your iPhone or iPod touch. (Note: you can configure only one Exchange account per device.) On your iPhone or iPod, tap Settings In the Settings menu, tap Mail then Contacts, then Calendars, then Add Account, then Microsoft Exchange. On the next screen (shown […]
Just because your business network is small doesn’t mean that hackers won’t target you. The reality is that automated scanning techniques don’t care whether your network is large or small. The look for and exploit common security holes in network security regardless of size, which is why outsourcing your IT to an IT firm is one […]