Nobody likes getting a bill. Even less 1000 bills. We engage with customers all the time that work with our competition that do hourly IT support. Every time they pick up the phone to talk about anything, the client gets a bill. They call us because they are fed up. Death by 1000 papercuts. Luckily, […]
As you progress from startup, to small business, to medium sized business you’ll likely experience some growing pains. Frequently those are related to technology. We call them the 6 stages of IT support grief. None of them except for the last are good for your business. We’ll share our observations and what you can do […]
Source: Pixabay.com We live in an age of disruption, thanks to artificial intelligence. Businesses are getting transformed. Our working habits are getting transformed. And even our lifestyles have massively changed since the dawn of AI. Today, AI is an important necessity in our homes—and sometimes even a household presence (Hi Alexa). If you thought you […]
Many businesses are looking for opportunities to save on costs going into 2021. IT is one place that many businesses can save money with better management. Here are IT Cost Saving Tips. IT Cost Saving Tips – Audit Systems A great place to start is to understand what you currently have in place and what […]
COVID-19 has changed the way the world works. Working from home is commonplace and it looks like that’s here to stay. Being forced to make the change to work from home has helped businesses realize that many jobs can be done from home just as effectively. Businesses can potentially even recognize some savings by allowing […]
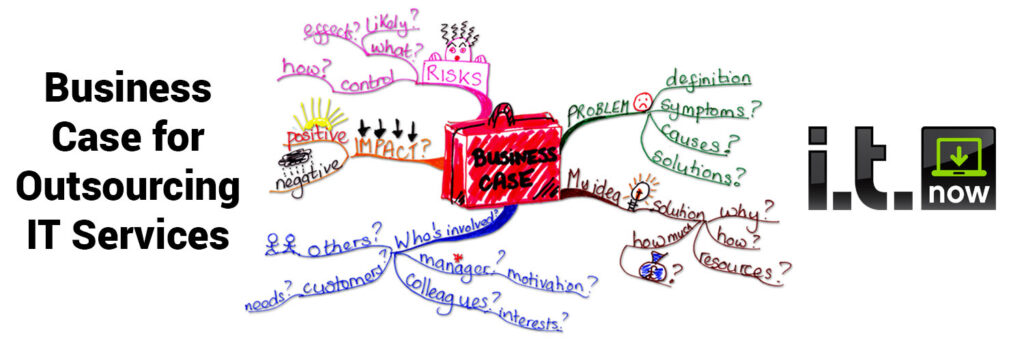
“TechAisle reports that as of 2015, at least 40% of small businesses in the US will have had made the switch to an external IT management service.” There are a lot of reasons why a company might want to outsource IT support. We hope that this article can serve as a template for those looking […]
Most small businesses have limited time and resources they can spend on network security. That’s just the reality of the situation. When consulting with small business owners, one of the most common questions I get asked is, “What are the most important things I can do for my network security?” The implication behind this question […]
We’ve had some clients come to us with battery woes lately. So, we did some research and have the scoop on how to get the most out of your battery. The original inquiry was about a laptop battery, but the principles we learned can apply to most portable electronics. Here are our tips on how […]
Twas the week before Christmas, and the office went out No computer, no internet…not even a mouse No work was getting done as tempers flared Bob called the IT guy who said he’d be there The managers were frustrated with deadlines ahead Would sales make their quota, the president said Many hours later, with everyone […]
Do Not Use These Passwords! If there is one thing that we can all agree on, it’s that 2020 has been a dumpster fire. The only thing that would make it worse is if someone hacked your password and stole your data. We’re here for you. I present a list of the 100 worst passwords […]