Windows 8 has upped the traditional desktop operating system. Its colorful tiles are now easily moved and accessed with a touch of your finger. But for those who have their Windows 8 system installed on a non-touch screen computer, the tiles can, at first, be difficult to use. How do your open the different applications, […]
Category Archives: Basic Computer Info
Servers are a critical piece of your business network and the hardware that they run on should be carefully selected to fit your specific business needs. There are a few guidelines that you should follow that will allow you to have a greater return on your hardware investment and lower support costs. From a support […]
We’ve talked previously about the different types of dangers that can threaten your computer. Malware, adware, spyware, and viruses can all cause havoc with your system. However, these malicious types of software are not the only avenues through which a computer hacker can access your information. If you use a computer network that is attached […]
While many shortcuts are similar on both PC and Mac computers, a Mac has a few different keys that make its shortcuts slightly different. If you are new to a Mac, transitioning from a PC, or simply want to know how to do your work faster on your Mac, here are a few of the […]
For those of you who love your PC and are constantly on the lookout for ways to improve your performance, this is a list for you. Keyboard shortcuts can help improve the speed with which you perform basic functions, helping you eliminate the clunky necessity of moving back and forth between your keyboard and your […]
Too often, computer and network security is not thought about until a problem arises. At this point, a breach in security can cause huge and potentially harmful problems to your business and/or your customers. By setting up a security plan and an emergency action plan, you can know that the information held in your computers […]
Having reliable data is a critical component of running a successful business. It can help you to make really good decisions and prevent you from making really bad ones. One area of business information that is often sorely neglected and overlooked is technology data and reporting. Having some good data on the status of your […]
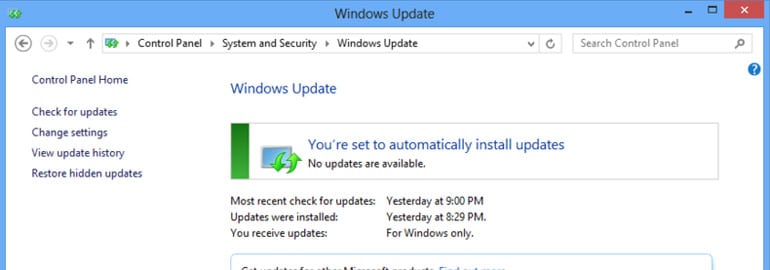
We’ve all had Microsoft Windows pop up and let us know that it needs to be updated at one point or another. What are those updates? Are they important? What happens if I don’t do them? They are important, and they do need to be done. Here’s why. Microsoft updates are basically broken into 4 […]
You hear all the time about identity theft and online fraud. But you think you’re not at risk, right? Think again. Identity theft is one of the fastest growing Internet crimes! The easiest way to protect yourself from identity theft is with a strong password. You have one of those, right? The best passwords, according […]
Jail breaking is the process of hacking a device (typically a smartphone or tablet) to bypass the digital rights management software usually installed by the hardware’s designer. This software exists to limit the type and amount of software or apps that can be run on a device. By jail breaking a device, users can have […]