Users of the 3CX voip phone system should be on high alert. A new 3CX security vulnerability has been discovered which can deliver malicious payloads. This attack is worse than most because it is a supply chain attack. That means that the bad actors have managed to get their malicious code incorporated into the legitimate installer for the application.
How it Happened
3CX Ceo Nick Galea confirmed the presence of the threat Thursday morning in a forum post. He noted that the installer for the 3CX desktop application includes malware, and users should uninstall it immediately. There is an alternate PWA client that is not infected users can use in the meantime while they are working on a clean release of the desktop app.
3CX developers apparently used bundled libraries as part of their development process. Those libraries were complied as part of the 3CX installer and contain the malware. The 3CX team was unaware until a few days ago when the malware was detected by Sentinel One and other detection platforms.
The infected installer has been available on their website for free download for some time.
The Threat
The attack starts when the installer is downloaded from the 3CX website, or an update is applied to the already installed desktop application. When the installer package is loaded or the update applied it extracts malicious files to perform the next step of the attack.
“The malicious activity includes beaconing to actor-controlled infrastructure, deployment of second-stage payloads, and, in a small number of cases, hands-on-keyboard activity,” CrowdStrike’s threat intel team said.
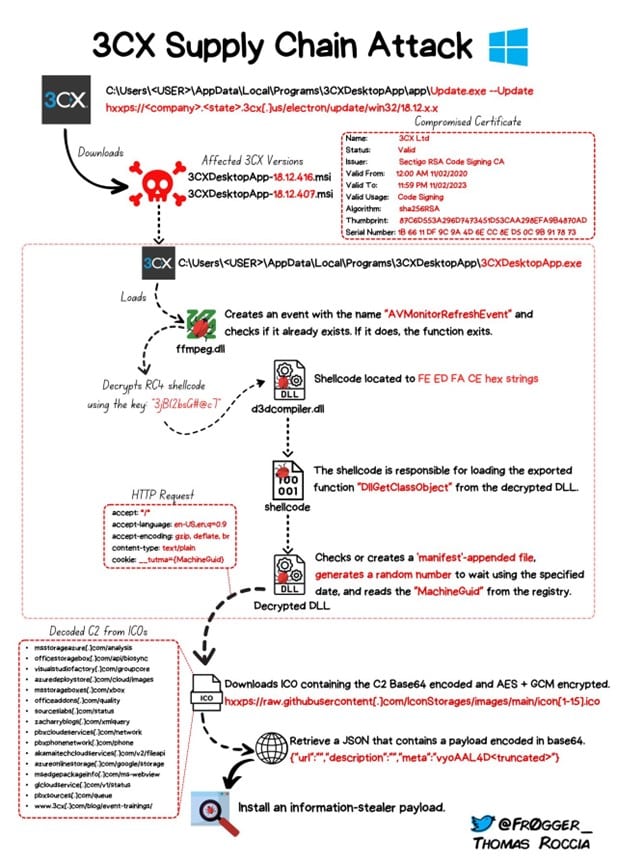
Thomas Roccia put together nice graphic that outlines the specific of how the attack happens.
Remediation Recommendations
Users that have the 3CX desktop client should contact an IT professional to assist you with remediation. Based on the current recommendations we’re seeing online from security professionals here are some quick remediation recommendations.
- Locate the 3CX desktop application in your environment and uninstall it from all machines.
- Ensure that endpoint detection and response software is deployed to all applicable systems.
- Scan the machine to attempt to detect any residual malware.
- Stay tuned for more advice as this one evolves.
Illustration by Thomas Roccia
Header Image Photo by Pixabay: https://www.pexels.com/photo/blur-bright-business-codes-207580/