Multi Factor Authentication
According to a recent study by the SANS institute up to 99.9% of attacks can be blocked with multi-factor authentication. If your organization hasn’t already put some form of MFA in place to protect your client data, you’re behind the times. Here’s why MFA is so important.
Some Threat Statistics from Microsoft
- 9% of attacks can be blocked with MFA
- 4000 daily ransomware attacks
- 300,000,000 daily fraudulent sign-in attempts
- 167,000,000 daily malware attacks
- 81% of breaches are caused by credential theft
- 73% of passwords are duplicates
- 50% of employees use apps that aren’t approved by the enterprise
That paints a pretty stark picture. The threats are real, and our passwords are a big part of the problem.
We’re Bad at Passwords
So why are humans so bad at using passwords? Well the simple answer is that we’re lazy. If we used passphrases that were complex and unique for every single login that we had in our life it would go a long way. The problem is that gets unpractical real fast. Stop for a second to count all the accounts that you log into daily. You log in to your computer, then log in to several different applications for work. Next you log in to different websites and log in to stream a tv show. Digital Guardian reports that users have an average of 90 accounts online. Its simply not practical to try and remember 90 complex passwords. The difficulty in remembering passwords drives risky behavior.
- 18% of users reuse the same password
- 39% of users write them down on a piece of paper
- 10% keep them on a file on their computer
- 7% keep them in a file on dropbox or similar service
So, if we’re so bad at passwords, what is the solution? MFA is here to stay.
Multi Factor Authentication Definition
Onelogin gives us a working definition of MFA. Multi-Factor Authentication (MFA) is a security system that verifies a user’s identity by requiring multiple credentials. When it comes to MFA, we typically refer to three types of authentication factors:
- Information you know, such as a password or PIN
- Things you have (possession), such as a badge or smartphone
- Things you are (inheritance), indicated through biometrics, like fingerprints or voice recognition
Most of you have probably used MFA at sometime without even realizing it. A good example is online banking. When you log into your account from a new computer it will send a code to your cell phone. You then must enter that code into the browser before it will authenticate you. Sometimes it will also require a fingerprint scan on your phone as well to log you in. It will typically look like this.
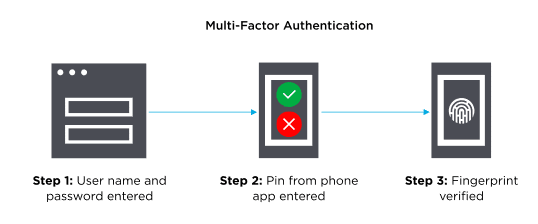
Some new advanced MFA technologies will look at additional factors as well. Where are you logging in from? What time of day are you trying to gain access? What device are you using? Is the network you’re using public or private? All these factors and more are being used to verify your identity and keep your data safe.
What had Slowed Adoption of Multi Factor Authentication?
Well there are a couple of misconceptions about MFA that have kept some people from adopting it. Some organizations have concern about potential user disruption, or that it may break something. There are also some folks that think that MFA still requires a dongle or other security hardware. This is not the case for most modern MFA solutions. No matter what the reasons, its time to get some better security in place. MFA has proven to be an easy effective way to protect your crucial data and stay safe online. Its time to make plans to put it in place for your organization.
How Can I Get Started?
One of the easiest ways to get multi factor authentication put in place is to get yourself a good authenticator app on your cell phone. Duo gives us a good rundown of how these apps typically work. Typically, a 2FA transaction happens like this:
- The user logs in to the website or service with their username and password.
- Password is validated by an authentication server, and if correct, the user becomes eligible for the second factor.
- The authentication server sends a unique code to the user’s second-factor device.
- The user confirms their identity by approving the additional authentication from their second-factor device.
There is a little bit of setup involved, but once you have the authenticator app set up they are pretty slick to use and don’t take as much time as you would think. There are several good authenticator apps worth looking at on the market. Gizmodo gives a good rundown. I’ll mention their top 5 briefly.
- Google Authenticator
- Microsoft Authenticator
- Authy
- LastPass
- Duo Mobile
There are a lot of others that will likely do the job as well, but these ones are some of the most popular. Authy is my personal favorite for ease of use. It’s a free download so give it a shot.
Multi Factor Authentication for your business
Setting up MFA for your business applications and data can be a little more complex. If you use Microsoft Office 365 Suite MFA is a built-in feature you simply need to turn on. They give you a nice walk-through on how to do it here. Google’s gsuite has similar features and their own walk-through you can check out. MFA can also be enabled on recent versions of Microsoft Server. They have a walk-through for that here. What about your those other applications that are specific to your business? How do you secure those? That answer isn’t as straightforward. Many software manufacturers have started including MFA as an option for their logins, so that’s a great place to start. If you have access to the admin settings on that software look for security features and see if there is a toggle to turn MFA on. It may require an authenticator app like the ones mentioned above to function. If that is the case set it up on the app and you’ll likely be good to go. Not all software manufacturers support MFA. That makes those applications much harder to secure. If this is the case for you reach out to the software manufacturer and see what can be done. If they have enough requests most software manufacturers will fast track that feature into the next update. You may need to repeat this process if your business uses multiple applications and logins. Think about all the places you keep data and work to secure them if possible.
In Summary
99.9% of attacks can be blocked with MFA! What are you waiting for? Take the time to secure your business data today. You won’t regret it. It’s easy to use, won’t slow you down, and could mean the difference between a happy safe business and one that got breeched. If this process seems overwhelming or you need help with other IT security concerns i.t.NOW stands ready to help. We have over 20 years’ experience securing clients networks and protecting their data. We can help you put the right solutions like MFA in place so you can have confidence your data is safe. Give us a call today!