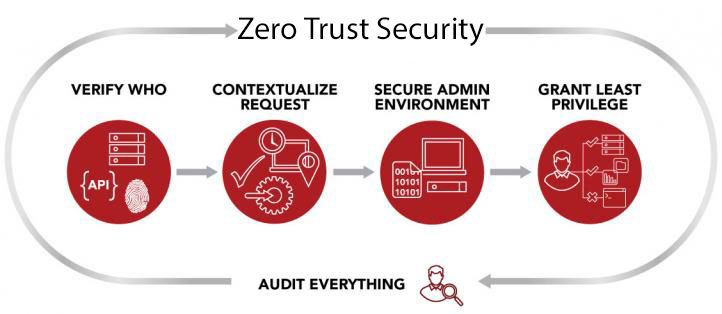
The idea of zero trust security has been around for several years. It has grown in popularity rapidly through 2020 and 2021 as Covid 19 has forced many businesses to work from home and looks to become the new standard for securing a mobile workforce. It will be key to most security strategies moving forward and all business owners should consider how it’s tenants can benefit their business.
IBM gives us this definition of Zero Trust Security.

In other words, we deal with security the same way that Ronald Regan dealt with Russia – “Trust but verify.”
Perimeter Security Model
To understand why the no trust model is so different and how it can help with today’s unique security challenges we have to look at how we’ve been doing security for a lot of years. The perimeter security model.
For many years most businesses have had most of their sensitive data and applications housed internally on servers they hosted themselves. To protect that data, they worked hard to secure the perimeter of the network. They used firewalls and other network-based tools to inspect and validate users entering and existing the network. The entire goal was to keep the bad guys out.
The challenge that many businesses have identified over the last few years is that their applications and critical data frequently don’t reside within the confines of their office network anymore. Their users too could be connecting from home or elsewhere with a variety of devices that IT can’t control.
These changes necessitate a change in the way we secure our data as well.
How Zero Trust Security Can Solve Today’s Problems
Zero Trust security can be effective at securing today’s networks because it looks at security differently from the perimeter security model. Instead of working simply to keep bad guys out, it works to continually verify that the users that do have access should based on numerous factors. Crowdstrike has some good resources on it.
Essentially zero trust solutions are continually looking at real time visibility into user and application identity attributes such as:
- User identity and type of credential (human, programmatic)
- Credential privileges on each device
- Normal connections for the credential and device (behavior patterns)
- Endpoint hardware type and function
- Geo location
- Firmware versions
- Authentication protocol and risk
- Operating system versions and patch levels
- Applications installed on endpoint
- Security or incident detections including suspicious activity and attack recognition
Users are authenticated beyond a doubt any time when requesting access to company resources and data. It also allows users to be connecting from any location on any device. Every time access is granted, they are verified at that point in time.
This facilitates secure access to applications and data outside the primary network and plays nice with both work from home and BYOD (Bring Your Own Device) which have become necessary. It also makes securing various cloud resources, SASS applications, and other data points outside the network easier to secure and manage for IT.
Conclusion
There is a lot to think about with zero trust security. There is complexity into planning a move from traditional perimeter security to a zero-trust architecture. However, as the IT solutions we use continue to change and evolve outside the network it will likely become necessary for most businesses to adapt their security posture as well.
i.t.NOW can help. We offer a free network security evaluation and can advice you on how to secure what is most important to you. Give us a call today.