Multifactor Authentication has become a part of our modern world. Its an essential part of a network security plan. However, hackers are using evolving attacks to defeat MFA. Let’s look at some of those attacks and see what can be done to protect against them.
What is Multifactor Authentication?
“Deploying MFA means you require more than one authentication factor to identify a user, so if one factor is compromised, there is a second or even third token standing between attackers and your company data. While strong authentication truly is the cornerstone of good security, it’s important to note that there’s no such thing as a silver bullet in this industry and that cybercriminals have found ways to bypass MFA protections.”
SMS Attack
Text has been used for multifactor authentication for quite a while now. Although convenient, it’s one of the least secure options for MFA. Hackers can intercept, phish, and spoof text messages. They are also vulnerable to sim swapping. This is where an attacker swaps the sim from your smartphone into another device to intercept any MFA codes sent to the device via text. We recommend choosing another method for MFA wherever possible such as an authenticator app to help prevent SMS attacks.
One Time Passwords (OTP)
OTP codes are another widely used form of MFA. Generally, these codes are secure. Like most MFA methods they can be compromised through social engineering. Someone with stolen credentials could convince you to share the OTP code or use a phishing attack to get you to enter the information in a fraudulent website. An advanced email security suite can offer protection against phishing, and end user security training can help humans to recognize social engineering, so they don’t fall for it.
Mobile Push
Applications such as Duo on a smartphone allow for mobile push MFA. The duo app simply pops up an approve or deny box when MFA is requested. The request comes from the app and is the most secure of the methods mentioned. The user experience is dead simple and has advantages for users that get easily confused.
One thing to watch out for is auto approval thumb. Some users get so used to clicking that green check when they see it that they don’t stop to think about whether MFA has been requested and approve when they shouldn’t. One thing you can do to aide users is to ensure that your MFA requests show the users location of origin. If an MFA request comes in from Russia hopefully that catches your user’s eye, so they deny it.
Evolution of MFA Attacks – Pass The Cookie
Attackers keep evolving along with security, and the pass the cookie attack is a good example of the next generation of threats that we need to protect against. Microsoft summed up this attack beautifully.
A “pass-the-cookie” attack is a type of attack where an attacker can bypass authentication controls by compromising browser cookies. At a high level, browser cookies allow web applications to store user authentication information. This allows a website to keep you signed in and not constantly prompt for credentials every time you click a new page.
“Pass-the-cookie” is like pass-the-hash or pass-the-ticket attacks in Active Directory. After authentication to Azure AD via a browser, a cookie is created and stored for that session. If an attacker can compromise a device and extract the browser cookies, they could pass that cookie into a separate web browser on another system, bypassing security checkpoints along the way. Users who are accessing corporate resources on personal devices are especially at risk. Personal devices often have weaker security controls than corporate-managed devices and IT staff lack visibility to those devices to determine compromise. They also have additional attack vectors, such as personal email addresses or social media accounts users may access on the same device. Attackers can compromise these systems and steal the authentication cookies associated with both personal accounts and the users’ corporate credentials.
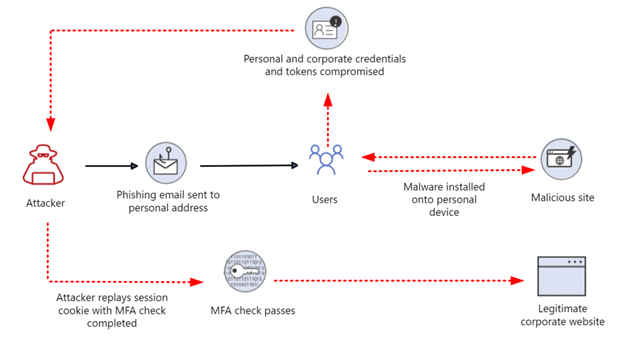
Commodity credential theft malware like Emotet, Redline, IcedID, and more all have built-in functionality to extract and exfiltrate browser cookies. Additionally, the attacker does not have to know the compromised account password or even the email address for this to work— those details are held within the cookie.
To prevent the risk of sustaining a pass-the-cookie attack, reduce the lifetime of those cookies or tokens wherever possible, and educate users about the threat.
Conclusion
Having the right security in place is important. MFA is an amazing solution that can prevent most attacks. Users need to be aware of the risks of the different forms of MFA and how to stay safe online. IT admins should choose the MFA solutions they use for their organizations carefully and educate their users on the advantages and risk of what they decide.


