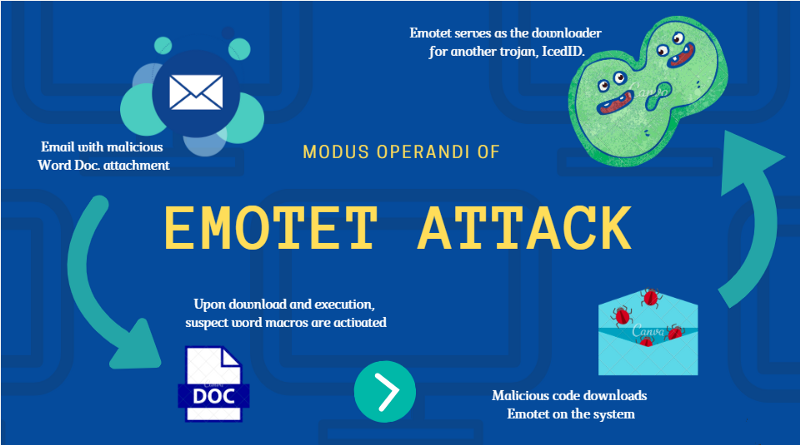
For several years bad actors have been using Emotet malware and its variants in large scale phishing attacks. These attacks are meant to compromise business email accounts and then allow them to deliver a payload of ransomware. Some recent updates from Microsoft have made those attacks less effective, so the hackers have had to pivot.
Emotet 1.0
The original strategy used in conjunction with Emotet malware was to deliver phishing emails with Microsoft office attachments that contained macros or VBA scripts. These common attachments appear safe and normal, and garnered a lot of clicks.
Users did not know that when they opened the attachments it executed macros within the documents that would install the emotet malware. Once installed, bad actors can use this as a jump point to install ransomware or launch other attacks into the network.
This worked well for quite a while, but in Feb of 2022 Microsoft released a patch to secure the macros in their office documents and the phishing campaigns have become less effective. The groups behind the attacks have decided it’s time to pivot and switch up their attack path.
New Attack Path
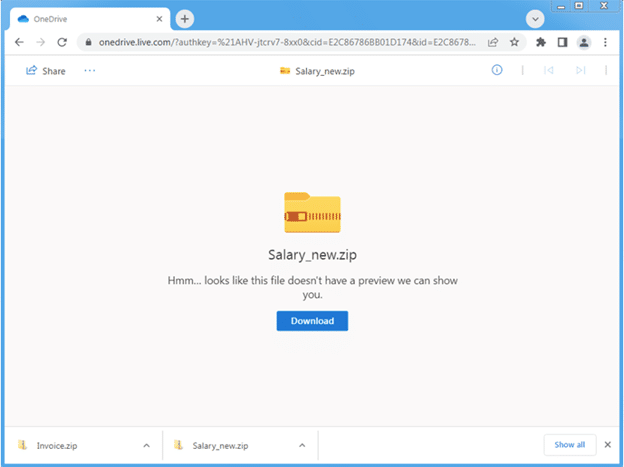
The new strategy uses compromised email accounts to deliver messages that contain a OneDrive URL.
Threat Post gave us some information,
“This URL hosts Zip files containing Microsoft Excel Add-inn (XLL) files. When these XLL files are opened and executed, Emotet will infect the machine with malware. Further it can steal the information or create a backdoor for deploying other malwares to compromise the Windows system.”
The bad actors appear to have been testing these new methods at a small scale for a period of several months to gauge their effectiveness. Now they have a proof of concept, and have started to put them into full production again ramping up widespread phishing campaigns.
How to Stay Protected
Users should look out for sketchy emails typically with a one-word subject line mean to garner interest and a link to OneDrive. Don’t click on it and delete the email immediately and you should be fine. They look something like this.
If your organization is not up to date on patches with Microsoft you may still be vulnerable to the Emotet 1.0 attack set. Talk to your IT department and ensure that your machines are kept up to date for protection from this and future attacks.
Here to Help
The security experts at i.t.NOW are here to help. If any of this sounds daunting, or you don’t have time for it, give us a call. Protecting your business from cyber threats should be a high priority. An ounce of prevention and education is worth a pound of cure. We are happy to help businesses recover from an attack when needed, but we’re much more pleased when we can stop one from happening in the first place. Call us today with your IT Security questions!