Technology is supposed to make things simpler. Changing IT solutions and a terrifying threat landscape have created a rush of new products and services. The complexity of Network security has increased 10-fold over the past few years. IT professionals are hurrying to keep up, understand what’s relevant and implement needed solutions with the moving target […]
Over the last few weeks, we’ve been talking to a lot of businesses that are looking for help. One thing that struck us is that they all seemed to have different reasons for reaching out. We can solve a lot of different business problems. These have been interesting and fruitful discussions, and we’ve boiled them […]
A robust onboarding process ensures that 69% of employees remain with the firm for 3 years. Why not consider using security technologies if you’re looking for ways to improve your onboarding process? How can security technologies improve the onboarding process? Keep reading to discover why security technologies are valuable to the onboarding process. Learn about […]
We met with some business owners this week where the current IT provider has neglected their technology for some time. There were a few contributing reasons for this. The client is in manufacturing and is hesitant to invest money in technology that they didn’t see improving their production process or output. The current solution was […]
There have been a lot of changes over the last few years to how we work. The rise of work from home has brought with it several new challenges like recovering your business hardware from terminated WFH employees. We have seen a few different businesses’ takes on that and have been involved on the IT […]
There is a lot of debate around backing up data stored in cloud solutions and SaaS applications. Office 365 backups are at the center of that debate. So, do you need to backup data stored in your SaaS apps? That depends. Do you need to backup data stored in Office 365? Almost certainly. Responsibility model […]
Since back in 2008 Verizon has been putting out a report each year called the Data Breach Investigation Report (DBIR). In 2013 they first wrote about ransomware. Social engineering was already happening and growing in popularity with bad actors. The latest edition of DBIR shows that 9 years later Ransomware and Social Engineering are still […]
I recently attended an IT industry conference where the topics were understandably cyber security heavy. One of the speakers that stuck out to me was Scott Augenbaum. Scott is a retired FBI agent that worked in the cybercrimes division for the last 20 years and has recently retired. A few things from his address stuck […]
As the saying goes, you’re only as strong as your weakest link, and in the case of cybersecurity, your weakest link is humans. With the new security challenges brought about by remote work, humans have become more of a cyber risk than ever. As of 2022, 88% of data breaches are caused by human error. […]
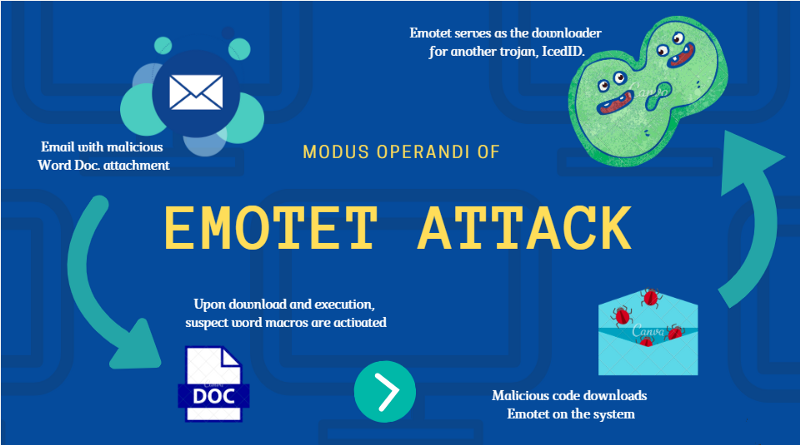
For several years bad actors have been using Emotet malware and its variants in large scale phishing attacks. These attacks are meant to compromise business email accounts and then allow them to deliver a payload of ransomware. Some recent updates from Microsoft have made those attacks less effective, so the hackers have had to pivot. […]