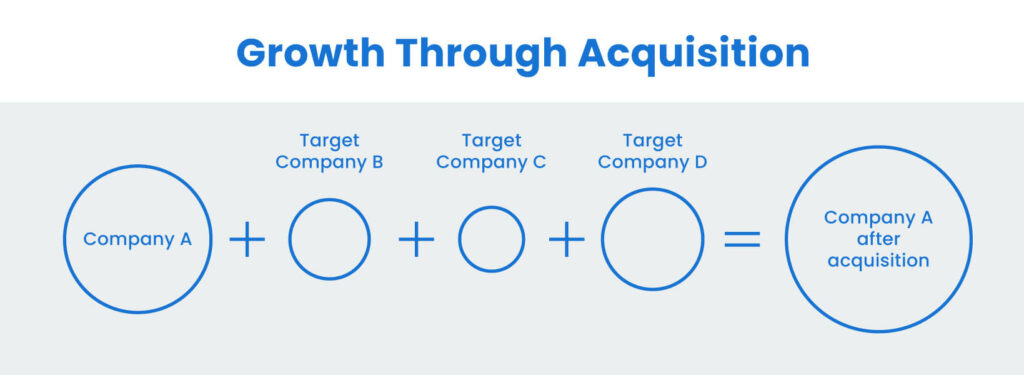
Recently we’ve been having a lot of conversations with companies that operate on the strategy of growth by acquisition. They span various industries. Property management, skilled nursing, assisted living, and most recently volleyball clubs. Regardless of the business vertical they are all buying new properties/facilities/clubs to fuel their growth. With that comes some potentially unique […]
There are a lot of business reasons why you may want to send encrypted email. It could be sensitive financial data, or personal information about employees. Maybe you work in healthcare and need to send personal health information that is protected by HIPAA. There could be several other reasons. There’s also not only one way […]
Digital inclination has brought about a new wave of cybercrime, with cyberattacks increasing at an unprecedented rate. Statistics from Abnormal revealed that phishing had a growth rate of 48% from previous years as of June 2022. Unfortunately, small and medium businesses (SMBs) are a common target for cybercriminals, accounting for 43% of cyberattacks in 2019 […]
We’ve been told for some time that there are dangers associated to connecting to free public Wi-Fi. What are those dangers? Could they put your data at risk? We’ll look at a few of the most common threats associated with public Wi-Fi, and how to stay protected. MITM Attack One of the biggest dangers with […]
To succeed in solving complex problems, you must learn active listening. The entire objective when sitting with a client is to seek to understand. Not only understand the problems they’re facing, but WHY they are a problem. What are their motivations for wanting a solution? Listen more and speak less. Ask for clarification and questions […]
In a discovery meeting with a potential client this week we discussed a long list of challenges they have with their current IT provider. Really long. They have been with them for over 7 years. Then he raised an interesting objection. He said, “I just don’t want to leave one set of problems for another […]
In the past, businesses either had an internal IT person/team or they worked with an outsourced IT company that provided Break/Fix or Managed IT Services. As the model has developed, businesses are finding it advantageous to have a combination of in-house and outsourced IT. For instance, they may not have the budget or need for […]
Co-managed IT support has been gaining popularity with business owners and executives because it offers flexible, simple solutions to complex IT problems. It also allows them to maximize the efficiency of their IT team and save on labor costs. In this guide, we’ll take a deeper dive into what co-managed IT support is, potential use […]
There is a shift happening in the marketplace where businesses are increasingly choosing to outsource specific roles to Managed Service Providers. There is a realization that it is not effective for larger entities to outsource all IT roles. After 100+ endpoints, it’s important to have an internal IT manager or team. However, the IT budget […]
i.t.NOW works hard to protect our clients’ networks from security threats and ensure their safety and operability. In those efforts we frequently see what growing threats there are in the wild. Two that we particularly wanted to make our clients aware of are Business Email Compromise (BEC) attacks, and Ransomware. Neither one of these attacks […]