Multifactor Authentication has become a part of our modern world. Its an essential part of a network security plan. However, hackers are using evolving attacks to defeat MFA. Let’s look at some of those attacks and see what can be done to protect against them. What is Multifactor Authentication? “Deploying MFA means you require more […]
They how and why of cybersecurity are numerous and varied. Here we’ll discuss endpoint attacks specifically, and some of the more common attack vectors. We’ll also touch on a few primary ways to prevent these breaches, and why business owners should care. How are they getting in? Here are several common attack types User Initiated […]
In a recent conversation with a business owner, they disclosed that they were going through a BEC (Business Email Compromise) attack on their network. There are a lot of email threats out there, but this attack was worse than most. The attackers gained access to their email, monitored activity to see who they corresponded with […]
Most organizations make cybersecurity overly complicated because “you should do it either way.” This is not a valid argument. Business owners have tons of “have to” being thrown at them every day. It’s extremely difficult to cut through the fluff and identify what is critical and what is just nice to have. We take the […]
Many companies have gravitated towards allowing a hybrid or fully remote work schedule for their employees. While the popularity of this model is rising, working remotely is still new to a lot of people, so it may take time to adjust. One of the biggest challenges to working remotely is creating a home office setup […]
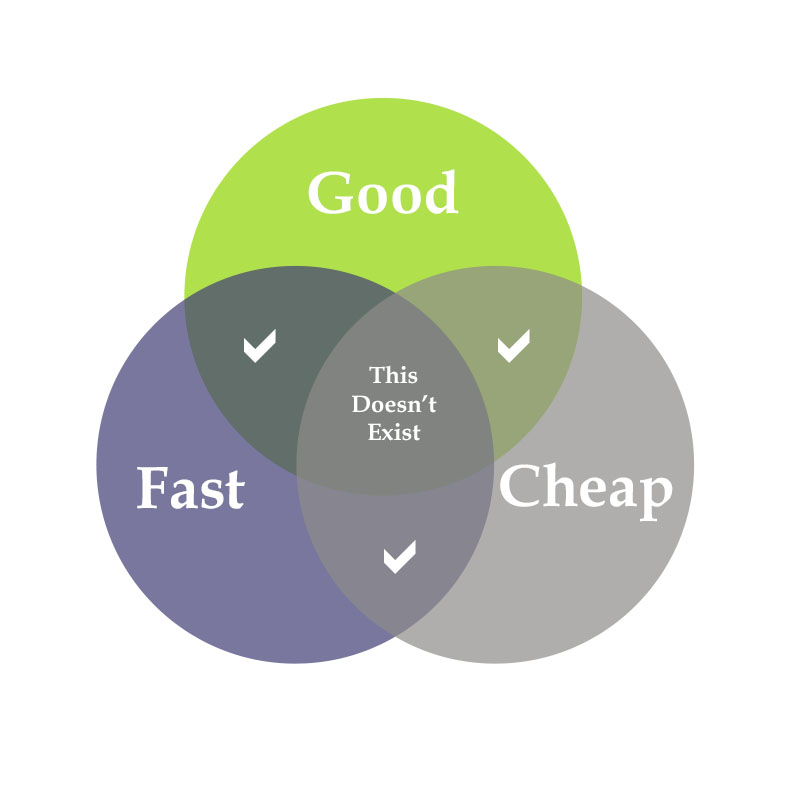
IT Services are like most things. You can get good support fast, but it usually won’t be cheap. Fast and cheap solutions are usually not good. Cheap good solutions are frequently not fast. See the diagram above. I call this the good, fast, cheap conundrum. A prospect called us this week that was referred to […]
In the last 24 hours there have been reports online of 2 zero day vulnerabilities that have been detected in Microsoft Exchange Server. These vulnerabilities only apply to On Premise Exchange versions 2013, 2016, and 2019. They do not apply to Microsoft Exchange Online which is part of the Office 365 Suite. What We Know […]
Shocking news rocked the IT world today when it was revealed that Microsoft has successfully quashed on premise Exchange email for small businesses. They haven’t stopped making or selling Exchange. You can still buy a current version and it’s even still supported. Microsoft has just made it prohibitively expensive vs the simpler, cheaper, easier to […]
News spread fast about a recent security breach at Eagle Mountain City that may end up costing taxpayers $1.13 Million Dollars. Limited information about the attack is available. There are a lot of things that could have been done to prevent it. What We Know KSL News reported on the breach. EAGLE MOUNTAIN, Utah– Officials […]
We’ve had a lot of conversations with clients recently that were trying to get covered with Cyber Security Insurance for the first time or going through a renewal. Claims paid out by cyber insurance companies have gone up significantly in the last few years because of ransomware, phishing, and other threats. Insurance companies are getting […]