The weakest link in most IT security plans is frequently your employees. Cyber security training can help them recognize threats and not fall for that phishing scam. Without it, a misguided click can subvert a lot of the other security you’ve worked hard to put in place. What is Cyber Security Training? People make mistakes. […]
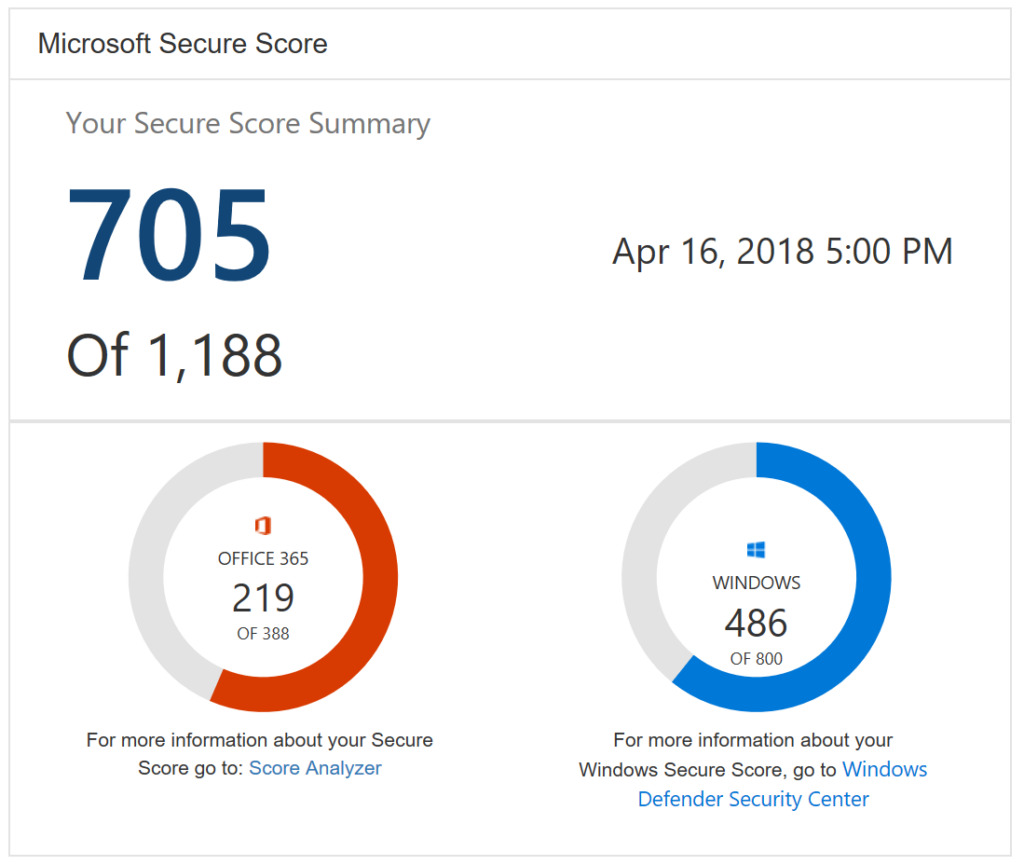
Businesses should always be on the lookout for ways that they can increase their security posture. Microsoft is aware of this and wants to help. They’ve created some built in functionality within Office 365 that assists organizations in improving their security. Here’s what it is and how it can help your business. What is Microsoft […]
With the rise of ransomware and increasing automated bot attacks the need for cyber liability insurance has never been higher than right now. Business owners often underestimate the cost of a breach or outage due to an attack. Having the right Cyber Liability insurance in place can help protect your business if you qualify. Security […]
Moving into 2022, cybersecurity is a hot topic. With hacking and data breaches on the rise, it is more important than ever for individuals and businesses to protect their digital information. You may think phishing is a hacking tool of the past, but hackers and cybercriminals still use phishing and social engineering to steal personal […]
In 2021, cybersecurity continued to be a top concern for businesses and individuals alike. Despite increased awareness and investment in cybersecurity solutions, there were still many high-profile cyberattacks that affected both organizations and individual users. When we see these high-profile attacks on the news, it’s important to use them as case studies so we can […]
HIPAA compliance is a critical part of protecting the privacy of patient information. It is also important for healthcare organizations to maintain HIPAA compliance in order to avoid potential fines and penalties. What is HIPAA Compliance? The Health Insurance Portability and Accountability Act (HIPAA) was created in an effort to standardize healthcare information in the […]
Recent discussions with a couple of different businesses identified a need for secure file sharing with their clients. Traditionally clients sent sensitive documents over email. This isn’t ideal. Plain text email can put your client’s data at risk. There are a lot of different ways to securely transfer the needed files. The key is to […]
As remote work has become more prevalent over the last couple of years, having a web-based file sharing platform has become more important than ever. Ensuring your team has access to the files they need from anywhere is important to their productivity. Microsoft has 3 different solutions. This may seem confusing, but they all serve […]
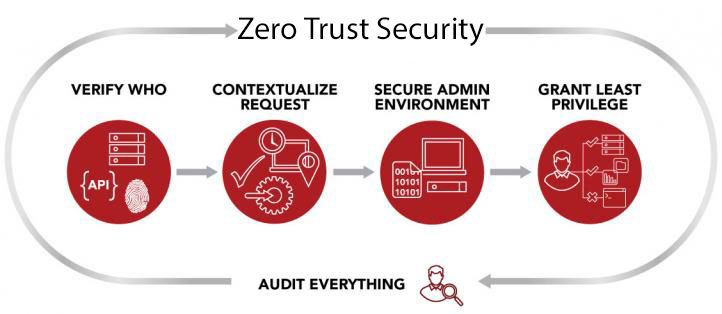
The idea of zero trust security has been around for several years. It has grown in popularity rapidly through 2020 and 2021 as Covid 19 has forced many businesses to work from home and looks to become the new standard for securing a mobile workforce. It will be key to most security strategies moving forward […]
Most IT guys are innocuous. On occasion, you find and IT guy that is well meaning but dangerous. How is he dangerous you ask? I’m not talking about him going rogue and sharing confidential data, or maliciously shutting down your network. The danger he poses is more accidental than purposeful, however it can still destroy […]