The reporting that most IT service providers give you isn’t great. This week I sat with a potential client that was frustrated with their current IT provider because they asked for a hardware inventory. What they got back was a long list of computer names and IP addresses. It honestly looked like nonsense to the […]
Category Archives: Managed Services
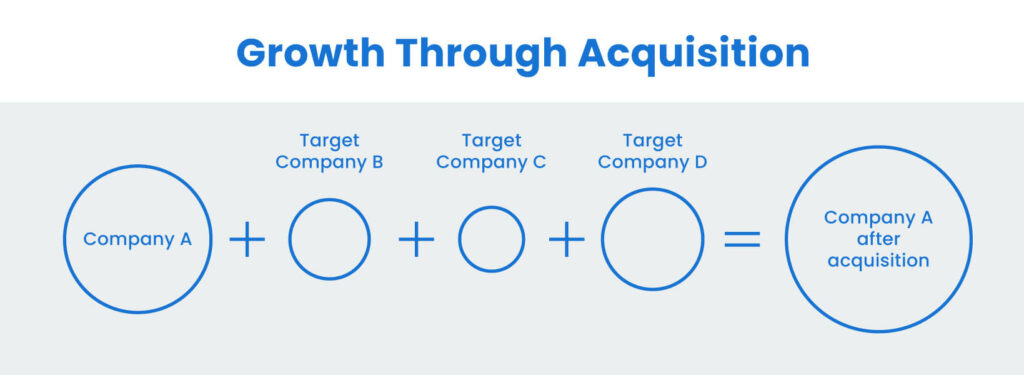
Recently we’ve been having a lot of conversations with companies that operate on the strategy of growth by acquisition. They span various industries. Property management, skilled nursing, assisted living, and most recently volleyball clubs. Regardless of the business vertical they are all buying new properties/facilities/clubs to fuel their growth. With that comes some potentially unique […]
To succeed in solving complex problems, you must learn active listening. The entire objective when sitting with a client is to seek to understand. Not only understand the problems they’re facing, but WHY they are a problem. What are their motivations for wanting a solution? Listen more and speak less. Ask for clarification and questions […]
In the past, businesses either had an internal IT person/team or they worked with an outsourced IT company that provided Break/Fix or Managed IT Services. As the model has developed, businesses are finding it advantageous to have a combination of in-house and outsourced IT. For instance, they may not have the budget or need for […]
Co-managed IT support has been gaining popularity with business owners and executives because it offers flexible, simple solutions to complex IT problems. It also allows them to maximize the efficiency of their IT team and save on labor costs. In this guide, we’ll take a deeper dive into what co-managed IT support is, potential use […]
There is a shift happening in the marketplace where businesses are increasingly choosing to outsource specific roles to Managed Service Providers. There is a realization that it is not effective for larger entities to outsource all IT roles. After 100+ endpoints, it’s important to have an internal IT manager or team. However, the IT budget […]
i.t.NOW works hard to protect our clients’ networks from security threats and ensure their safety and operability. In those efforts we frequently see what growing threats there are in the wild. Two that we particularly wanted to make our clients aware of are Business Email Compromise (BEC) attacks, and Ransomware. Neither one of these attacks […]
They how and why of cybersecurity are numerous and varied. Here we’ll discuss endpoint attacks specifically, and some of the more common attack vectors. We’ll also touch on a few primary ways to prevent these breaches, and why business owners should care. How are they getting in? Here are several common attack types User Initiated […]
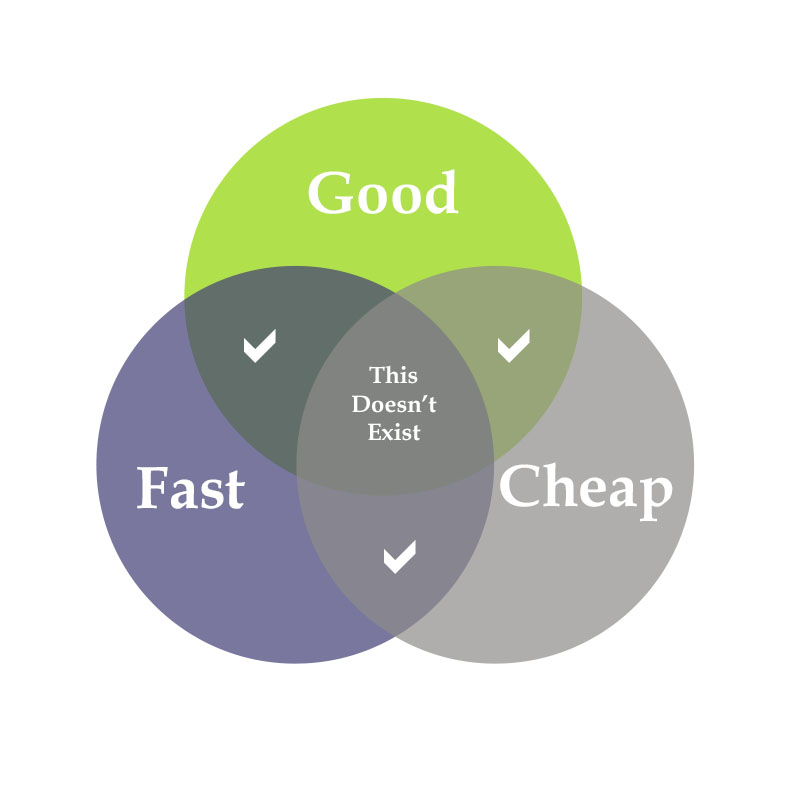
IT Services are like most things. You can get good support fast, but it usually won’t be cheap. Fast and cheap solutions are usually not good. Cheap good solutions are frequently not fast. See the diagram above. I call this the good, fast, cheap conundrum. A prospect called us this week that was referred to […]
I met with a company this week that is thriving. They have been growing by leaps and bounds over the last couple of years, and its run by smart, talented people. The one area where they are struggling is with managing their technology. That’s why they called me. They were essentially asking how to tell […]